 |
 |
The Internet of Things (IoT) promises to pioneer new ways for businesses to create value and organizations of all types are already benefiting from the new functionality and efficiency gains. However, the constant connectivity and data sharing through the anticipated 20.4 billion connected devices by 2020 (Gartner) also invites new opportunities to compromise security. |
By Emma Karhan, Head of Terrorism Specialty and Public Sector Partnerships at Aon’s Reinsurance Solutions business; Kelly Superczynski, Americas head of Capital Advisory team at Aon’s Reinsurance Solutions; Matt Wyckhouse, CEO at Finite State
Increasingly, connected devices for both personal and business use ushers in vulnerabilities that cyber-attackers can exploit. In fact, IoT devices are notoriously easy to infiltrate. NETSCOUT estimates that IoT devices are, on average, likely to be compromised within five minutes of connectivity to the Internet.
The rise of IoT devices has introduced an overlap of the physical and digital worlds, increasing dependence upon devices for critical business operations like physical security, building automation, energy management, industrial processes and transportation. In the IoT era, physical damage – like destroying a data center, shutting down a machine in a production facility or crashing a vehicle – is now possible from digital attacks.
These new and more prevalent IoT cyber risks present an opportunity for insurers to support organizations by raising awareness of risk management and exploring new cyber insurance products and services to provide protection.
IoT Changes Risk
IoT and other unmanaged devices increase exposure to typical cyber-loss events due to their growing volume and relative lack of security. Commoditization and globalization also play a role as most IoT devices involve a long, complex supply chain.
Catastrophic risks like business interruption, fire, explosion and sabotage can now be activated by hostile cyber actors. Attackers need only one trivial vulnerability to enter a network, and from there it’s relatively easy for them to take control.
Traditional IT security tools and methods simply do not work for IoT devices, partially due to their diversity and because they cannot easily be secured as they are black boxes. IoT device security varies from traditional enterprise security in many ways, including:
Visibility: Many organizations do not know what devices are on their network, and if they do, that is not enough: security teams must obtain deep visibility into the device including make, model and detailed vulnerability information about the firmware, which is the combination of software, applications, libraries, etc built into the device.
Vulnerability management: According to research by Finite State, only 1% of IoT vulnerabilities are reported about a specific device, but the underlying firmware often has numerous known common vulnerabilities and exposures (CVEs) that only the manufacturer can easily see.
Detection: Most security teams have visibility into what software is running on traditional IT devices and their traditional security processes are built around controlling user behavior to minimize risk. In the IoT era, end users rarely interact with the device and the risk, instead, is buried in the device firmware. Now specialized models and AI have been designed specifically for the unique behaviors of IoT devices to robustly detect attacks.
Response: Incident response on IoT devices is virtually impossible today, and new techniques are required to enable post-breach cleanup efforts.
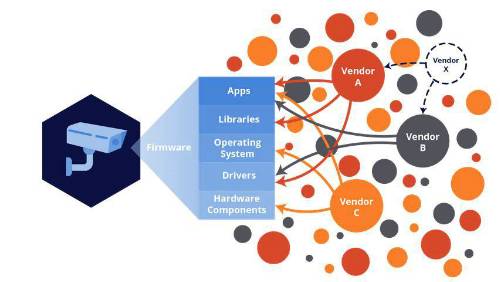
The firmware inside IOT devices is built from complex, global supply chains that could include vulnerabilities for hackers to exploit
This new risk demands a new response.
IoT Risk and Insurance
Traditional cyber insurance products cover privacy and security liability, cyber extortion, data restoration and incident response costs. In recent years, business interruption and contingent business interruption from both a breach or a systems failure has become a part of cyber insurance coverage. But to many insureds, these coverages can be confusing and may not provide the full scope required for all exposures. Executives are increasingly seeking products which cover property damage and bodily injury, which are increasingly importance due to IoT.
In many cases, the knock-on effects of cyber attacks involving tangible assets enter the realm of non-affirmative or ‘silent’ cyber risk. These are cyber exposures nestled within traditional property or general liability policies that were not worded by property and casualty underwriters to account for the proliferation of a technological new era. Insurers’ IoT cyber insurance potential remains largely untapped as they must first substantially innovate existing products to reflect evolving cyber risks.
Reinsurance will play an important role in the further development of cyber IoT insurance products. The potential frequency and severity of IoT attacks can result in large economic losses so insurers will need to spread that risk in order to be able to adequately protect their capital while sufficiently serving the industry. Cyber IoT re/insurance is a substantial growth opportunity for both insurers and reinsurers.
According to Aon’s Cyber Solutions, insurers are just beginning to incorporate high-level IoT inquiries into underwriting discussions – almost exclusively with larger, more regulated organizations that have an appointed Chief Information Security Officer (CISO).
This leaves smaller businesses and those less equipped to articulate their enterprise security posture in the dark. The Ponemon 2019 Intangible Asset Financial Statement found that just 28% of companies purchase cyber insurance. In a Darwinian era where rapid innovation is paramount for companies to stay competitive, uptake of new tech such as IoT is outpacing the planning and budgeting for the additional risk management entailed.
Managing IoT Cybersecurity Risk
IoT is the entry point of choice for cyber attacks. Attackers have an extreme advantage today because they know how to analyze IoT firmware and find trivial vulnerabilities. Until organizations are able to level the playing field, their entire network is at risk in ways unimaginable a decade ago.
Cyber analytics vendors have been able to provide insurers with an incremental solution thus far, based largely on noninvasive scans of external-facing network infrastructure. These scans, and the data harvested from them, can be translated into security scores and even used to inform pricing and catastrophe models. Such models have made rapid progress over the past two to three years, and insurers are steadily relying on them for aggregation and capital management.
However, IoT devices can only be captured in external scanning, which seldom occurs. The ability to scan internally-facing network endpoints accessed by IoT devices may offer a marked breakthrough in cyber analytics. This is key to understanding risk: obtaining visibility for both the devices running on the network and for the firmware.
Today, cyber security firm Finite State is using two decades of experience supporting the Fortune 500 and the US intelligence community to help build understanding through IoT device intelligence. This leverages advanced program analysis and deep learning to analyze each IoT device and its underlying firmware.
IoT security scan capabilities, coupled with cyber analytics vendor partnerships, could very well usher in a new era of progress for insurers to refine the modeling, pricing and cover for cyber risk – particularly as they may be covering these risks without fully understanding the implications. In addition, new and relevant products will enable insurers to drive growth in a rapidly growing market.
Companies that rely on IoT may be exposed to unforeseen risks that may not be insured today. Insurers, reinsurers and their customers must work together to understand, mitigate and transfer these new, complex risks in an increasingly IoT-driven world to achieve the opportunities in a safe and secure way.
|
|
|
|
| Take the lead client-facing projects ... | ||
| Various locations - Negotiable | ||
| Choose Life! Choose a major global co... | ||
| Various locations - Negotiable | ||
| Actuarial skillset? Apply now for Snr... | ||
| South East / hybrid with travel requirements - Negotiable | ||
| Financial Risk Leader - ALM Oversight | ||
| Flex / hybrid - Negotiable | ||
| Be the very model of a modern Capital... | ||
| London - Negotiable | ||
| Pensions Actuary seeking a high-impac... | ||
| London or Scotland / hybrid 3dpw office-based - Negotiable | ||
| Great opportunity for Pensions Actuar... | ||
| London or Scotland / hybrid 3dpw office-based - Negotiable | ||
| Responsible Investing Manager - Clima... | ||
| London/Hybrid - Negotiable | ||
| Quant Strategist | ||
| London/Hybrid - Negotiable | ||
| Multiple remote longevity contracts | ||
| Fully remote - Negotiable | ||
| Multiple remote inflation hedging con... | ||
| Fully remote - Negotiable | ||
| Play a vital role in shaping a new He... | ||
| London or Scotland / hybrid 50/50 - Negotiable | ||
| Support the Longevity team of a globa... | ||
| London / hybrid 2 days p/w office-based - Negotiable | ||
| Delve into financial risk within a ma... | ||
| Wales / South West / hybrid 1dpw office-based - Negotiable | ||
| Project-based Life Pricing Actuarial ... | ||
| South West / hybrid 2 dpw office-based - Negotiable | ||
| Pricing Actuary | ||
| London - £120,000 Per Annum | ||
| Develop your career in motor pricing | ||
| UK-wide / hybrid 2 dpm office-based - Negotiable | ||
| Experience real career growth in home... | ||
| UK-wide / hybrid 2 dpm office-based - Negotiable | ||
| Be at the cutting edge of technical p... | ||
| UK-wide / hybrid 2 dpm office-based - Negotiable | ||
| Use your passion for innovation and t... | ||
| London / hybrid 2 days p/w office-based - Negotiable | ||
Be the first to contribute to our definitive actuarial reference forum. Built by actuaries for actuaries.